The PUP Confusion Technique
I would like to demonstrate for you an antivirus detection evasion technique. I'll be using McAfee to demo this, but the problem exists in ALL personal antivirus software. Before we get going, I'd like you to meet two of my friends...
Cain
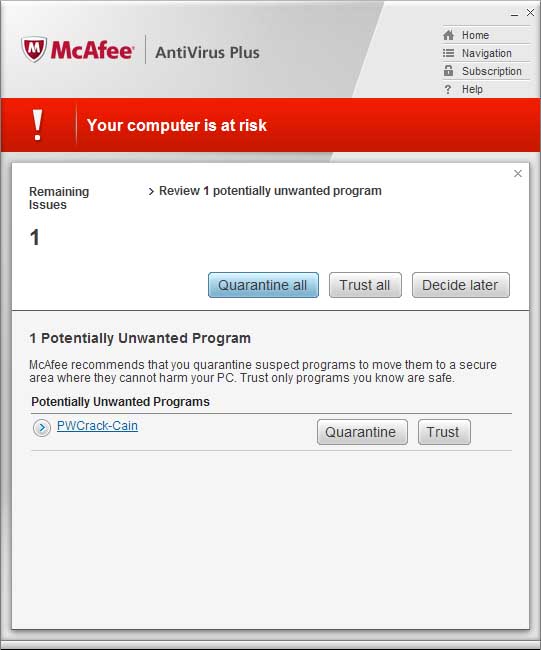
Cain is a pretty cool guy. Any Windows penetration tester has probably heard of him. He's really good at WEP cracking, password cracking, and network sniffing. A really cool tool for us hackers, but probably not something a sysadmin would want to find on one of their workstations. This kind of program is classified by antivirus programs as a Potentially Unwanted Program (or PUP for short).
Here's what McAfee has to say about him:
Bifrost
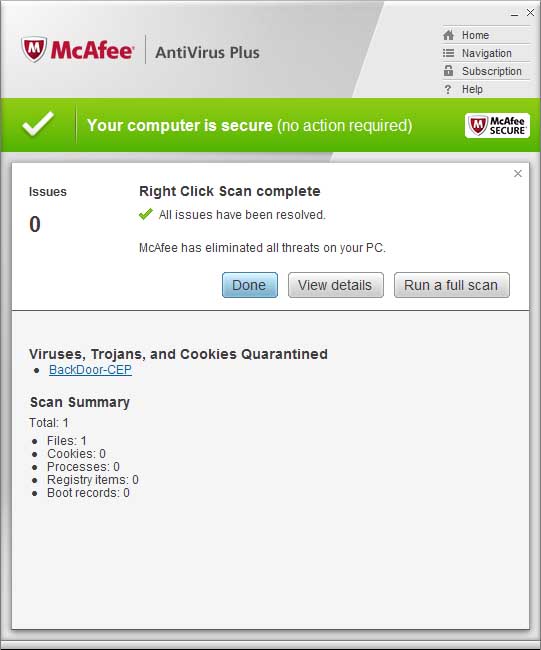
Bifrost was designed to be dangerous. His main purpose is to be a full featured, remote access backdoor to any Windows system. He's got so many dangerous features that you really should be scared of him. You definitely don't want this guy running on your PC. Bifrost is very well known, so antivirus software shouldn't have a problem detecting him.
Here's what McAfee has to say about him:
The Problem
Antivirus programs use signature databases and heuristic algorithms to determine if a file is a virus or not. This means they have to scan a file, and if this file matches any of their MANY virus definitions, it will be reported to the user as a variant of that virus.
We can use that to our advantage. All personal antivirus programs as of today only assign one "detection" to a file. It would violate our common sense if our antivirus program started telling us a single .exe is is two viruses at the same time, so they simply don't. It's one detection to a file and that's it.
Cain, being classified as a PUP, may not be detected by some antivirus software with default settings. Simply because antivirus companies want to avoid complaints about false positives. For this example I'm using McAfee, which detects PUPs by default, so I'll have to modify my attack scenario a little bit just to prove my point. Say you want a copy of Cain, but their website was down. You ask a friend that you don't really trust for a copy, and you scan the .exe he sends you just to make sure it's not backdoored.
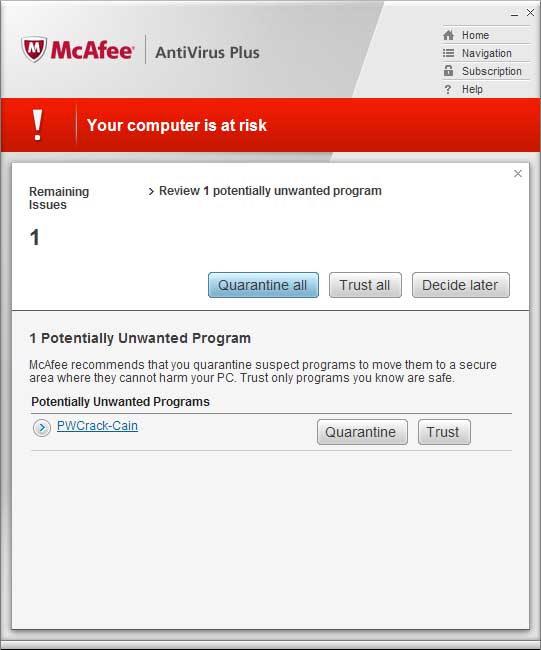
This problem, what I call the "PUP Confusion Technique", lets your "friend" make you run a backdoor program on your computer even if it is well known and easily detected by any AV software. The attack is simple. Append Cain to the Bifrost executable, and change the icon to look like Cain. When you append data to a .exe file it gets completely ignored by the operating system when it gets executed. Bifrost will still run like normal. The cool thing is: Even though executing the file runs Bifrost, Mcafee only detects the combination of Bifrost and Cain as "PWCrack-Cain." So, you, expecting to get a copy of Cain, won't suspect a thing when your AV is telling you the file is exactly what you think it is.
McAfee detects Bifrost as Cain:
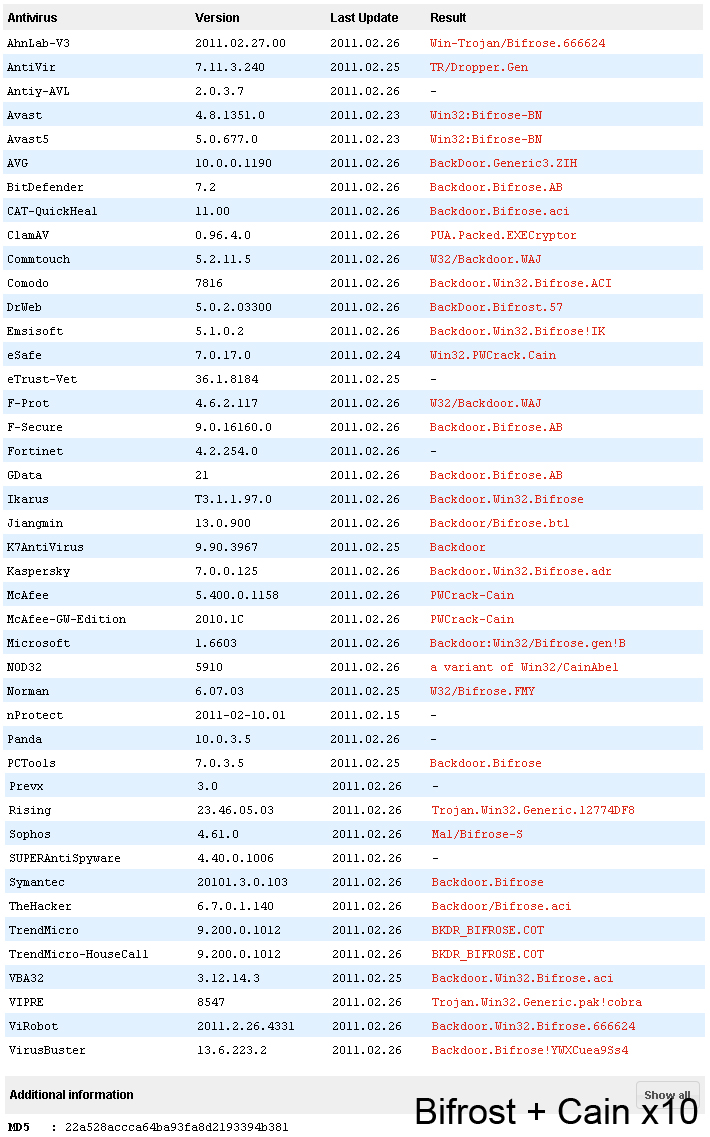
To see how many AVs fall for this trick, I uploaded Bifrost with 10 copies of Cain appended, to VirusTotal. Most detect it as Bifrost, but a few (Nod32, eSafe and McAfee) detect it as a Cain. Prevx, Panda, nProtect, and Avity don't detect anything at all, even though they detect "normal" Bifrost. With a little more work, it's probably possible to fool even more of them.
VirusTotal scan results:
VirusTotal Page Control Test - Cain Control Test - Bifrost
This attack can be improved too. Like I said, many AV software's default configuration is to ignore PUPs. If you append a bunch of PUP programs to the end of a real virus, it's very likely that the AV will detect the PUP first, and not even report it to the user. This is a very practical attack, and I would argue it's even more effective than hex editing or "crypting" undetection techniques.
You can imagine that once a file like this starts infecting lots of computers, AV software will automatically catch on. But once malware gets in, it could stop itself from being detected by disabling the AV software, or by making it's files larger than the "don't scan files larger than" setting in the AV.
This could also be used to sabotage legitimate software. If you appended a legitamete piece of software (or portions of it) to the end of a real virus, and distributed it throughout a botnet, AV software might catch on and start falsely reporting the legit software as a virus. I wouldn't be suprised of an evil software company did that to ruin their competition.
Test Files
You can use these files to test your antivirus software. This zip file contains Cain, Bifrost, Cain with Bifrost appended, and Bifrost with Cain appended.
WARNING: THE ZIP FILE CONTAINS VERY DANGEROUS PROGRAMS. DO NOT RUN THESE PROGRAMS, ONLY SCAN THEM.
I AM NOT RESPONSIBLE FOR WHAT HAPPENS TO YOUR COMPUTER IF YOU RUN THEM!
Copy and paste this URL into your browser and replace hxxp with http to download the file:
hxxps://defuse.ca/downloads/pupevasion.zip
Note: You will have to turn off your AV software to download and extract the file.
Note: Yes, I know I'm using the Bifrost builder and not an actual Bifrost server. It's just a demo, and the builder contains the server anyway.
The Solution
This is a fundamental problem with AV software. They only make one detection per file. The only way I can see this being fixed is if AV software starts reporting multiple detections per file, and that's a big change. Virus databases and multi-engine scanning services rely on the one detection per file model. However, I strongly urge all antivirus companies to take this technique seriously, and improve your products accordingly.
In the meantime, users of antivirus software can protect themselves by making sure PUP detection is turned ON and only obtaining software from the developer's website. Remember that antivirus software can't protect you from everything. Your best defense is being smart and only downloading what you trust and need.


